- Purpose of the Article: The purpose of the above article is to guide Android app developers in creating a robust security roadmap for their applications. It aims to educate developers about the importance of implementing secure coding practices and secure communication measures to protect user data and prevent unauthorized access.
- Intended Audience: the article aims to be informative and educational for Android app developers who want to ensure the security and protection of their applications and user data.
- Tools and Technology: OWASP Mobile Top 10, Android Jetpack Security, Firebase Authentication, OkHttp, JSON Web Tokens (JWT), SQLCipher, ProGuard, DexGuard, Google Play Services, OWASP ZAP, SonarQube, OWASP Incident Response.
- Keywords: Android app security, secure coding practices, secure communication, encryption, authentication, authorization, OWASP Mobile Top 10, Android Jetpack Security, OkHttp, Firebase Authentication, JSON Web Tokens (JWT), SQLCipher, Conceal, ProGuard, OWASP Dependency Check, DexGuard, Google Play Services, OWASP ZAP, SonarQube, incident response planning, user privacy, security testing.
Introduction
As Android app developers, we must ensure our applications are secure and use Secure Coding Practices to protect user data and prevent malicious actors from accessing any application or data. Securecommunication is a key component to any security roadmap for Android apps. In this blog , we will discuss the steps you can take to create a robust security roadmap for your Android app using Secure Coding Practices and Secure Communication. We will cover topics such as encryption, authentication, and authorization, as well as other strategies for making sure your app is secure. Let’s get started!
Secure Coding Practices
Follow Secure Coding guidelines provided by Android, such as avoiding hard coded credentials, using appropriate encryption algorithms, and validating user input. Implement input validation and output encoding techniques to prevent common vulnerabilities like SQL injection, cross-site scripting (XSS), and remote code execution.
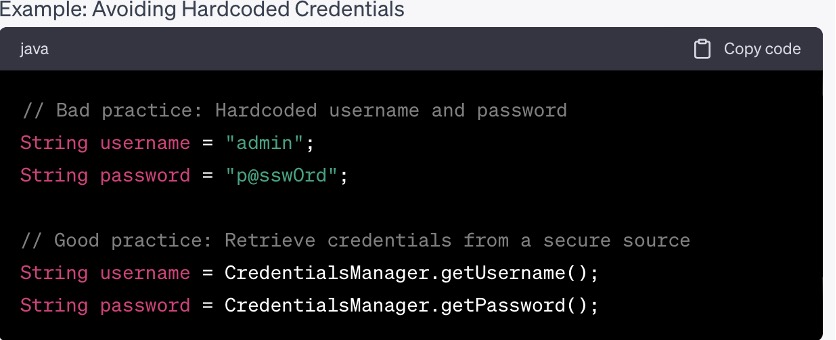
Library and Tools:
- OWASP Mobile Top 10: Follow the OWASP Mobile Top 10 project’s guidelines (https://owasp.org/www-project-mobile-top-10/ ) to address common security issues in mobile apps
- For Android Jetpack Security, Utilize the Android Jetpack Security library (https://developer.android.com/topic/security/data ) for secure data storage, including encryption and decryption of sensitive information
Secure Communication
Use secure communication protocols like HTTPS (TLS/SSL) to protect sensitive data transmitted between the app and the server. Implement certificate pinning to prevent man-in-the-middle attacks and verify the authenticity of the server’s SSL certificate.
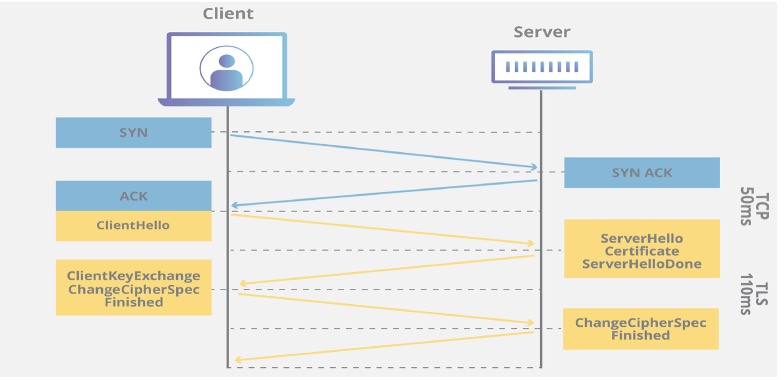
Library and Tools:
- OkHttp: Use the OkHttp library (https://square.github.io/okhttp/ ) to implement secure network communication, including support for TLS/SSL and certificate pinning
User Authentication and Authorization
Implement strong user authentication mechanisms, such as multi-factor authentication (MFA) or biometric authentication, to verify user identities. Implement proper session management techniques and enforce user authorization checks to ensure only users can access authorized resources.
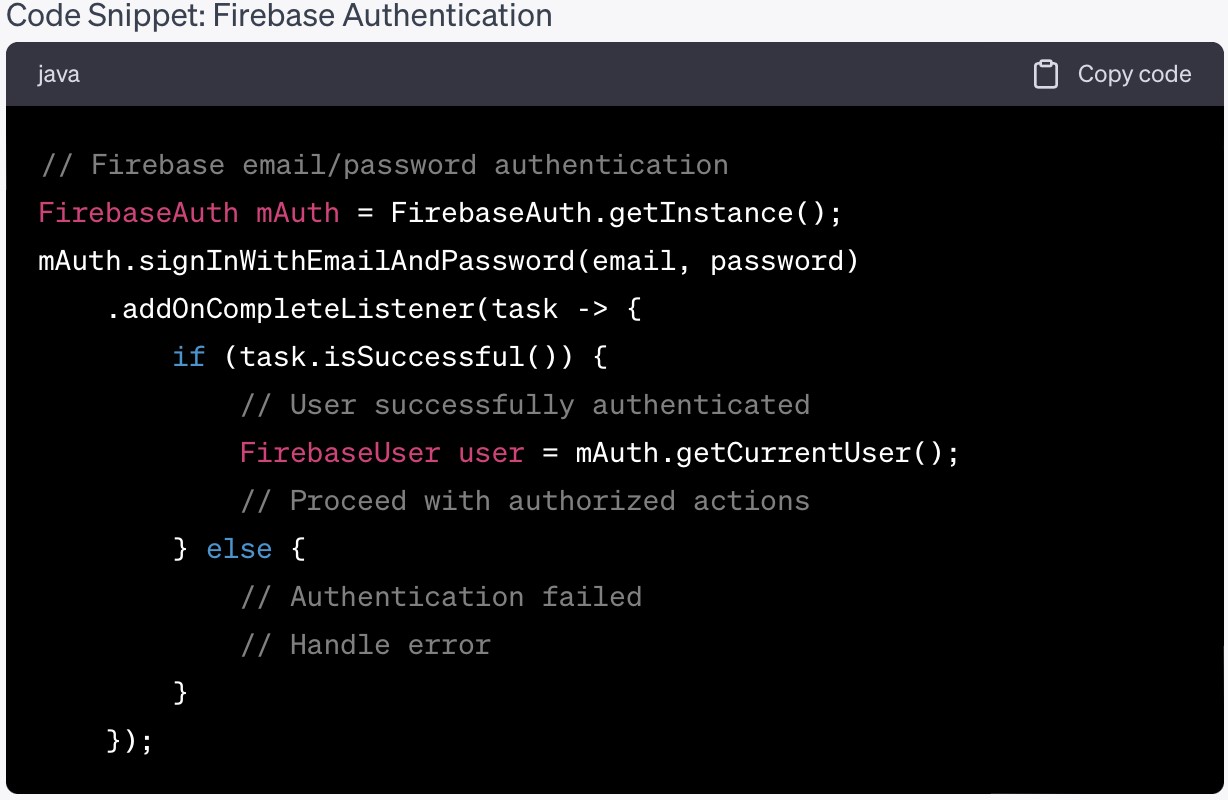
Library And Tools:
- Firebase Authentication: Integrate Firebase Authentication (https://firebase.google.com/products/auth ) to implement secure user authentication, including email/password, social logins, and multi-factor authentication
- JSON Web Tokens (JWT): Utilize libraries like jjwt (https://github.com/jwtk/jjwt ) to securely generate, sign, and verify JWT tokens for user authorization
Data Storage and Encryption
Encrypt sensitive data at rest using encryption libraries provided by Android, such as SQLCipher for local databases or Android Keystore System for secure key storage. Implement appropriate data storage mechanisms to prevent unauthorized access or leakage, like using SharedPreferences for sensitive configuration data.
Code Snippet: Using SQLCipher for local database encryption
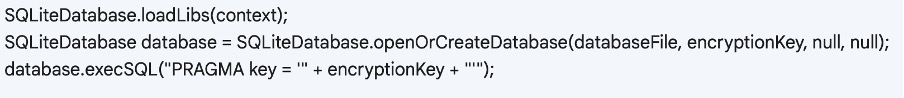
Library and Tools:
- SQLCipher: Implement SQLCipher (https://www.zetetic.net/sqlcipher/ ) to encrypt local databases, providing secure data storage on the device
- Conceal: Utilize the Conceal library (https://github.com/facebookarchive/conceal ) by Facebook for file-based encryption and secure storage of sensitive files
Secure Code and Dependency Management
Update the Android SDK, libraries, and dependencies used in your app regularly to include security patches and bug fixes. Perform code reviews and use static analysis tools to identify and fix security vulnerabilities in the codebase. Verify the reputation and security posture of third-party libraries and APIs before integrating them into your app.
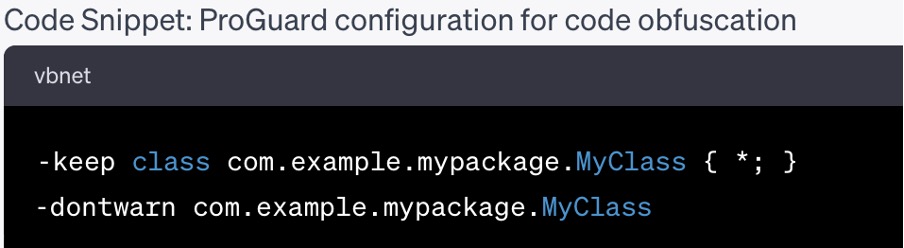
Library and Tools:
- ProGuard: Employ ProGuard (https://www.guardsquare.com/proguard ) to obfuscate and shrink your app’s code, making it more resistant to reverse engineering
- Dependency-Check: Utilize OWASP Dependency Check (https://owasp.org/www-project-dependency-check/ ) to identify known vulnerabilities in your app’s third-party libraries and dependencies
Secure Offline Storage
Implement secure storage mechanisms for offline data such as sensitive files or cached data, by leveraging encryption and obfuscation techniques. Avoid storing sensitive data in plain text or easily accessible locations within the device’s storage
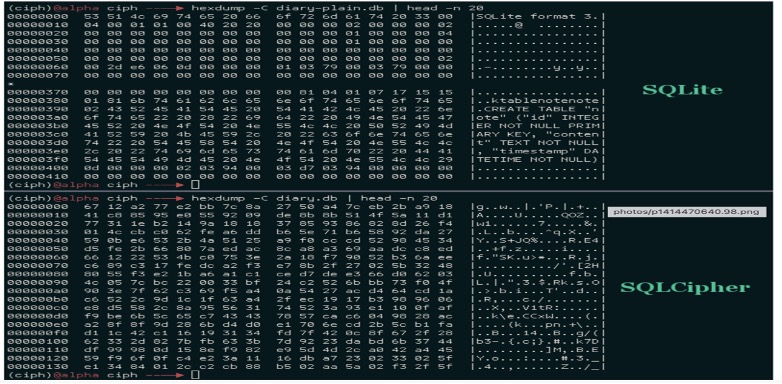
Library and Tools:
- SQLCipher: As mentioned earlier, SQLCipher is an excellent choice for encrypting and securing local databases used for offline storage
Runtime Protection
Implement runtime security measures like code obfuscation, anti-tampering techniques, and root/jailbreak detection to prevent reverse engineering and unauthorized modifications to the app.
Library and Tools:
- DexGuard: Leverage DexGuard (https://www.guardsquare.com/dexguard ) to protect your app against reverse engineering, tampering, and other runtime attacks
User Privacy
Clearly communicate your app’s data collection and usage practices to users, following privacy regulations and best practices. Obtain explicit user consent for collecting and processing personal information.
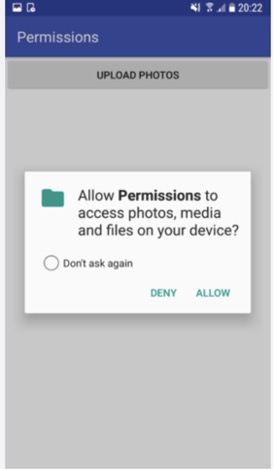
Library and Tools:
- Google Play Services: Integrate Google Play Services (https://developers.google.com/android/guides/overview ) to adhere to user privacy guidelines, including obtaining consent for data collection and processing
Security Testing
Conduct regular security assessments, including penetration testing and vulnerability scanning, to identify and address potential security flaws.Implement automated security testing tools to detect common vulnerabilities like insecure data storage, improper input validation, or weak cryptography.
Library and Tools:
- OWASP ZAP: Utilize OWASP ZAP (https://owasp.org/www-project-zap/ ) to perform dynamic application security testing (DAST) and identify security vulnerabilities in your app
- SonarQube: Integrate SonarQube (https://www.sonarqube.org/ ) for static code analysis to identify security vulnerabilities, code smells, and other code quality issues
Incident Response Plan
Develop an incident response plan to address security breaches or incidents promptly. Define roles and responsibilities, establish communication channels, and outline steps for containment, analysis, recovery, and communication in the event of a security incident
Library and Tools:
- OWASP Incident Response: Refer to the OWASP Incident Response project (https://owasp.org/www-project-incident-response/ ) for guidance on developing an effective incident response plan for security breaches and incidents
References:
Author Bio:

Tharun YEKBOTE
Technical Architect - Digital Transformation
I possess extensive experience in software development, specifically focused on creating diverse mobile applications such as Mobile & HMI Apps. Additionally, I excel in integrating cutting-edge AI technologies, including OpenCV and ML inference SDK, into Android platforms. Furthermore, I have a strong proficiency in incorporating IoT integration modules into software solutions. My leadership qualities further enhance my ability to effectively leverage digital technologies to drive successful outcomes.


